Security-Aware HARA introduction
[Author]
Samuel WENG, Safety + Secuity investigator
First: Background introduction
For cybersecurity, right now it is based on ISO SAE DIS 21434 or future editions, and they are propose one methodology called Threat Analysis and Risk Assessment. From here we could know each threat scenario can do how big damage to assets.
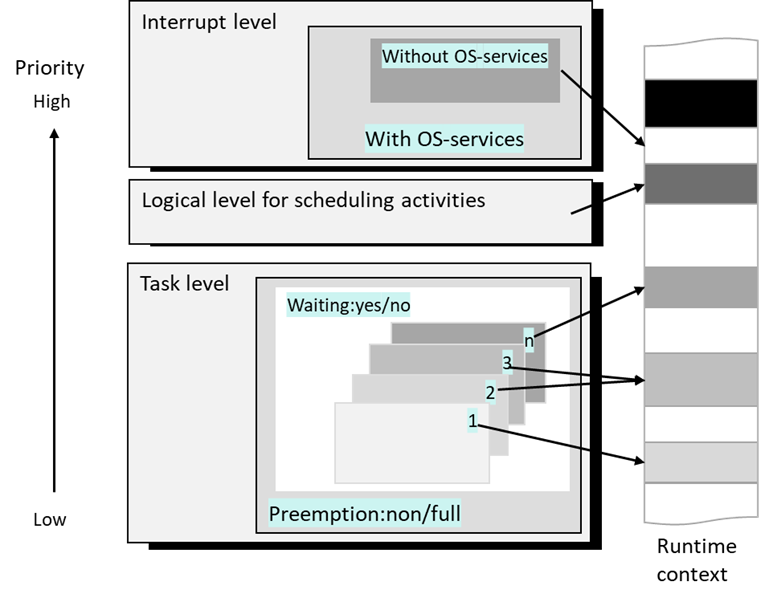
TARA original process listed as following:
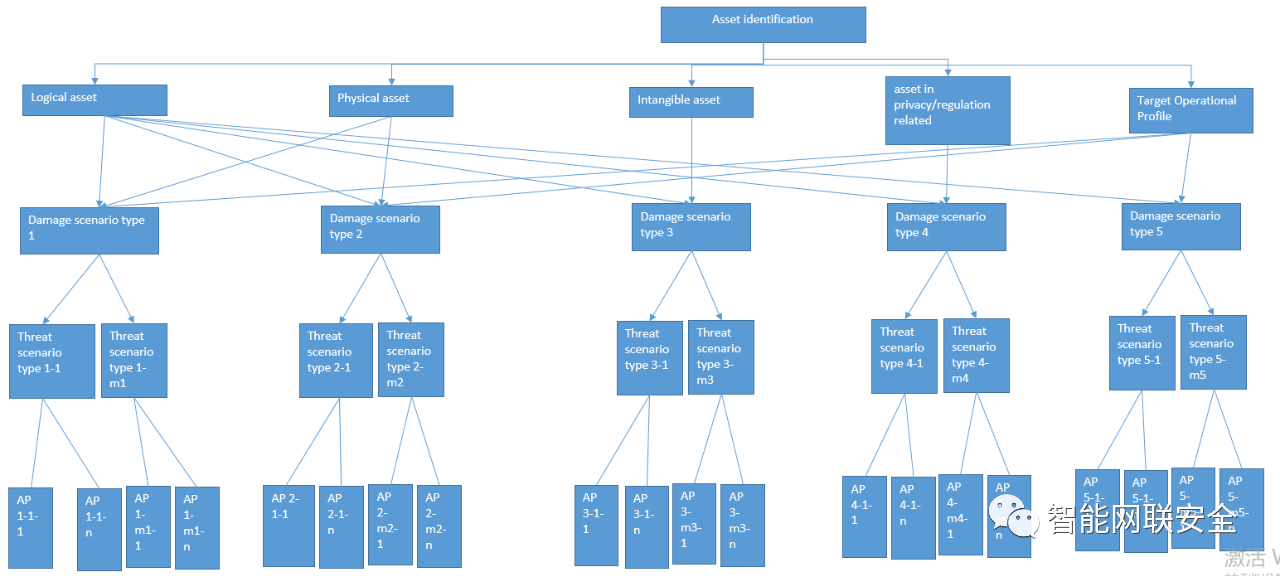
And then the final cybersecurity goals will coming out from here, and also IL to those SFOP or not.
Second: Problem ISO 21434 methodologyexisting
For first chapter, the ISO 21434 methodology some problems are existing:
1.the Attack path analysis methodology present only ATA way, but no systematic vulnerability side to explore
2.Not good analysis methodology or no valid methodology shown in ISO 21434 if dealing with ADS system or intelligent cockpit system
3.Not good recommendations on how to deal with those operations downsizing then how to deal with when in risk treatment, on which topic it is safety topic, but unfortunately this topic requires one guys shall sharply know safety and security.
Third: Proposal for Security-Aware Hazard Analysis and Risk Assessment (SAHARA)
Adapted from paper 'Threat and Risk Assessment Methodologies in the Automotive Domain' (www.sciencedirect.com), we are proposing one methodology for security aspect and to have better SOTIF or functional safety analysis dealing such cyber threats impacts.
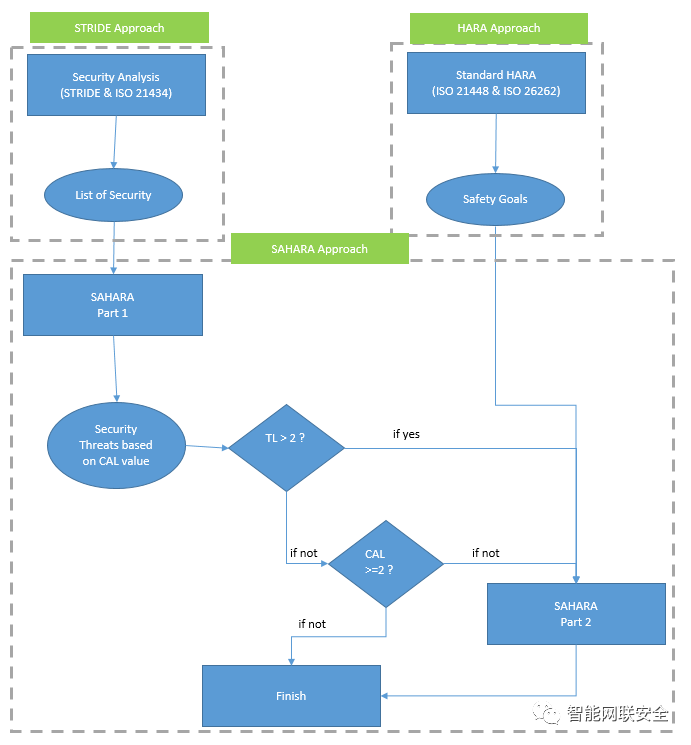
For SAHARA part 1, we can define directly from following risk matrix:
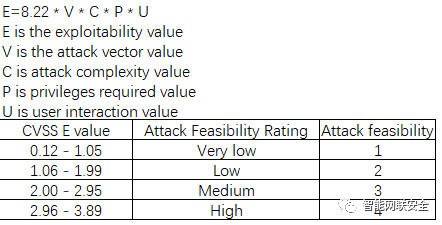
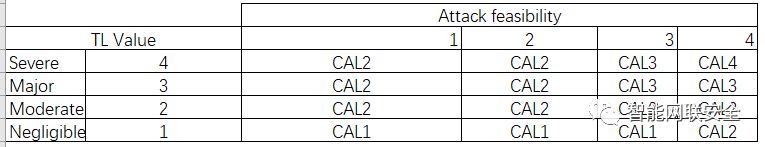
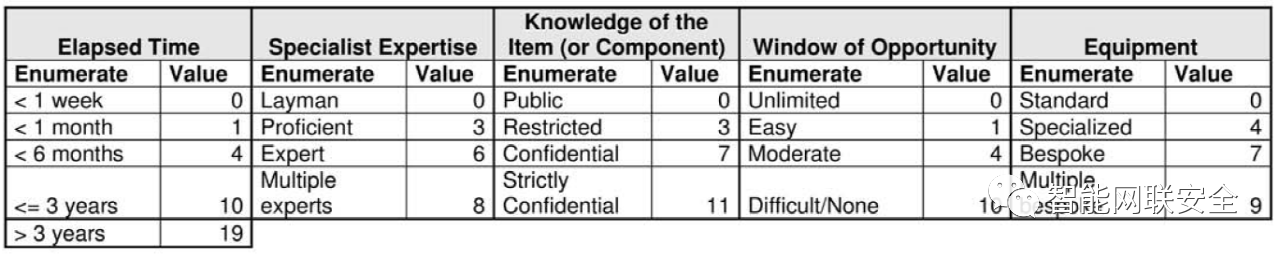
For SAHARA part 2, we get following features from ISO/IEC 18045, and then to put the following attack potential parameters:
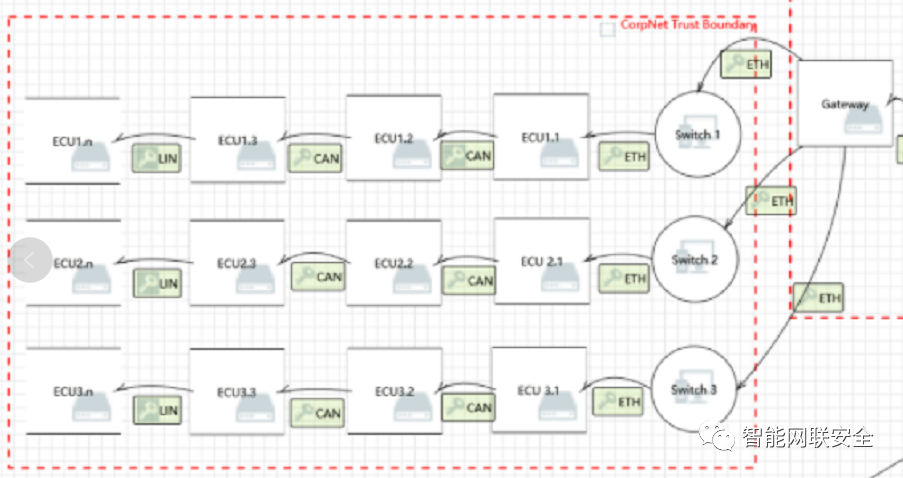
following, we just take 3 security hazards coming from https://mp.weixin.qq.com/s/GrhdFsDa8p7aSYxO9ugvAA
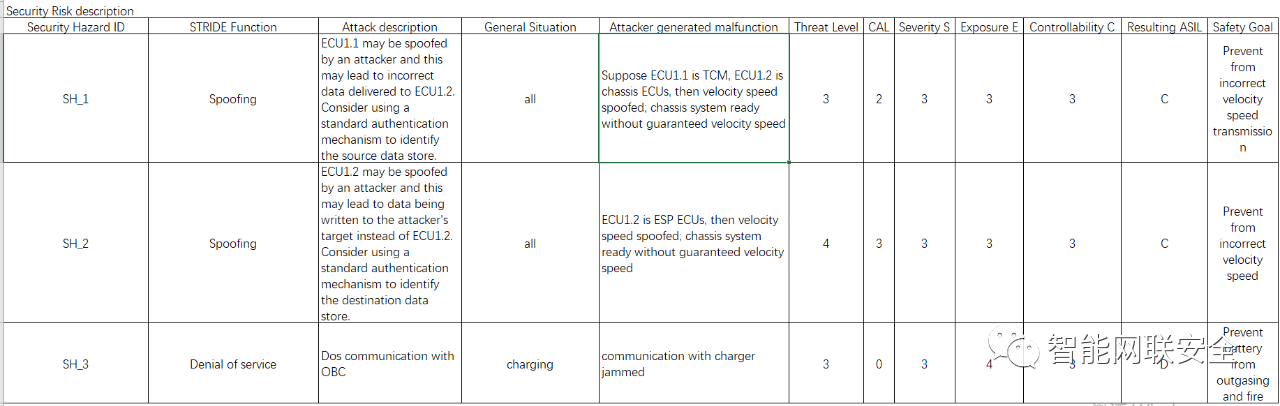
Finally, we got following Threat ratingsystems, since we have the attack feasibility value, then we can directlyabstract it from ISO 21434:
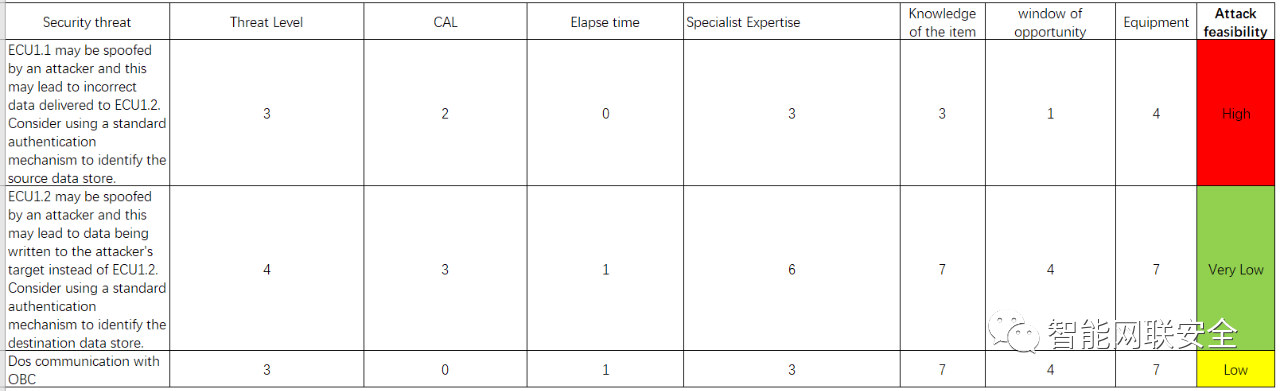
As you can see, for the attack feasbility, only the SH_1 are very high, and for other 2 secure hazards, attack feasibility not very high.
Conclusion:
safety and security are two challenging research domains for automotive systems. This article had modifed the methodology coming from one paper in reference, and then give out better guidance on how to give threat and risk assessment techniques available for the automotive domain and presents an approach to classify cyber-security threats and safety risks.
[Reference]
https://mp.weixin.qq.com/s/GrhdFsDa8p7aSYxO9ugvAA
Threat and Risk Assessment Methodologies inthe Automotive Domain' (www.sciencedirect.com)
ISO SAE DIS 21434
- 用户评论