CVSS and ISO/SAE DIS 21434
[Author]
Samuel WENG, system safety and security geek in automotive field
Being observed that the cyber security in the automotive field stronger and stronger, the ISO/SAE DIS 21434 coming in the beginning of this year.
This article will discuss the vulnerability within ISO/SAE DIS 21434
First: definition
Vulnerability is the weakness that can be exploited by a threat scenario, originated from ISO/IEC 27000-2016.
As you can imagine, the vulnerability canbe explained as following:

Within one thunderstorm night, one thieve want to steal assets like gold and silver jewelry from one house, here he has 3 potential paths:
1.directly go in the front door, break the door and get inside
2.go in the second route, and use Iron hammer break down windows and get inside
3.go to one tree, and climb up the tree, use the tree's path into the 2nd floor, and then get into the house.
Here, we can see that:
| Asset | gold and silver jewelry |
| property | confidentiality, anti-against those people touch it without authorization |
| threat | thieves, with some tools, like iron hammer, or bomb revenges technical researchers etc |
| vulnerability | front door without lock front door with bad quality lock No window window with bad quality tree get into 2nd floor 2nd floor has downstairs into 1st floor etc |
| attack feasibility | ??? |
| attack likelihood | ??? |
| vulnerability scoring | ??? |
from above, we can roughly to see, vulnerability forms into the the attack path, and as well the fragility within one system.
Second: vulnerability related contexts
we have to see how vulnerability acts within ISO/SAE DIS 21434, statistcs from ISO/SAE DIS 21434:
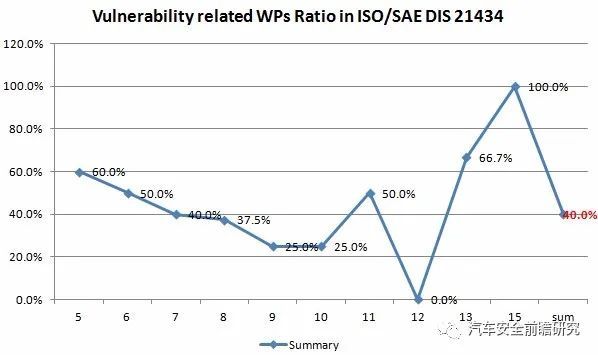
Almost 40% of cyber security activities relating to vulnerability, including management, control, reduce, treatment, incident response, etc.
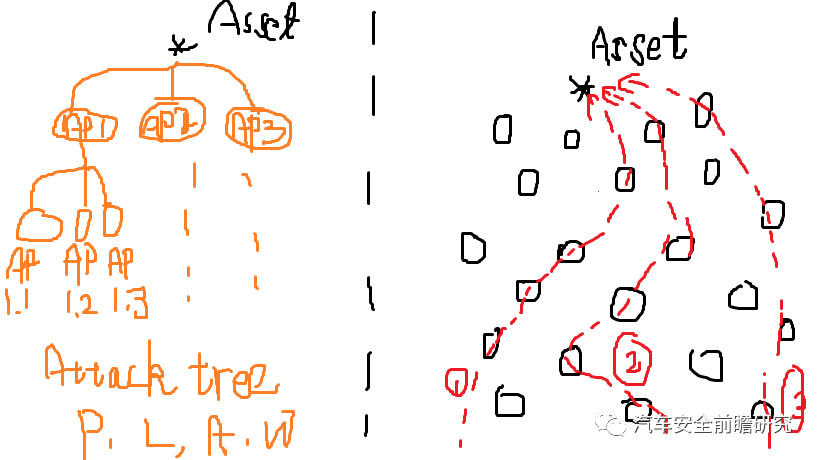
Especially in Threat Analysis and Risk Assessment, vulnerability forms into basis for attack path, there are two way for attack feasibility and likelyhood analysis:
1.vulnerability analysis
2.attack tree based
Third: CVSS
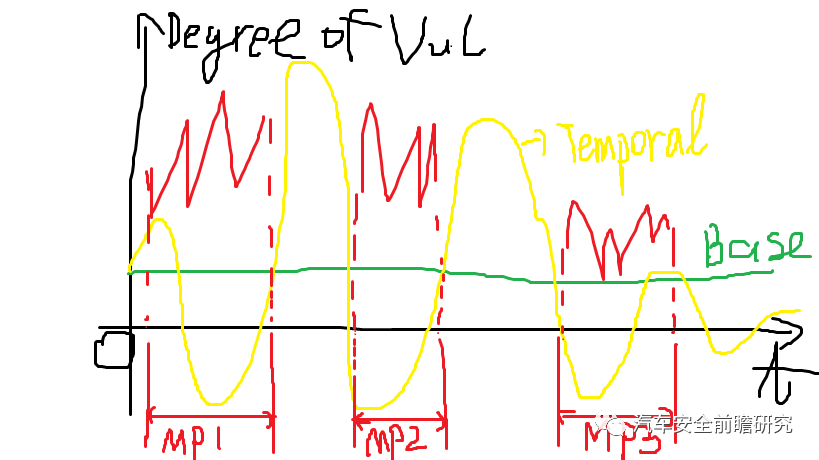
One way to measure vulnerability potential exploitation degree is the CVSS.
CVSS can be decomposed into following metrics:
1.Base metrics
2.Temporal metrics
3.Environmental metrics
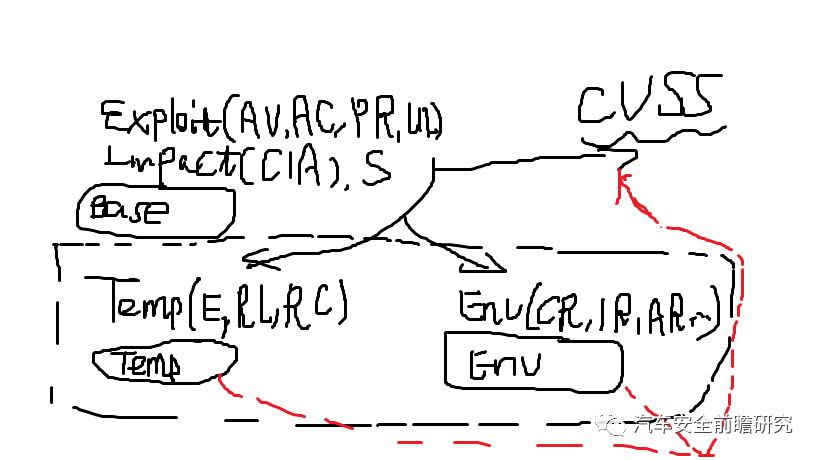
Third_1: Basic metric
basic metric represents the intrinsic characteristics of a vulnerability that are constant over time and across user environments, which is composed of two sets of metrics: Exploitability metrics, Impact metrics
For exploitability metrics:
(1) attack vector: network, Adjacent, Local, Physical
(2) attack complexity: Low, High
(3) privileges required: None, Low, High
(4) user interaction: None, Required
(5) scope: Unchanged, Changed
For impact metrics:
(1) confidentiality: High, Low, None
(2) integrity: High, Low, None
(3) Availability: High, Low, None
Third_2_Temporal_metric
Temporal metric includes exploit code maturity, remediation level, report confidence,
(1) Exploit code maturity: Not defined, High, Functional, Proof-of-concept, Unproven
(2) Remediation Level: Not Defined, Unavailable, Workaround, Temporary Fix, Official Fix
(3) Report confidence: Not defined, Confirmed, Reasonable, Unknown,
Third_3_Environmental_metric
Environmental metric includes modified base metrics, CIA requirement
(1) Security requirements: Not defined, High, Medium, Low,
(2) Modified base metrics: Modified AV, Modified AC, Modified PR, Modified UI, Modified S, Modified C, Modified I, Modified A
Forth: Qualitative Severity Rating Scale
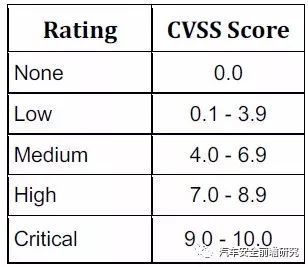
Fifth: House vulnerability CVSS scoring calculation
1.front door without lock


2.front door with bad quality lock


3.No window


4.window with bad quality


Synthesis:
| front door without lock | front door with bad quality lock | No window | window with bad quality | |
| base score | 7.9 | 5.6 | 7.9 | 5.8 |
| Temporal score | 6.6 | 4.8 | 6.9 | 5.2 |
Thanks for your reading, given well, please transfer.
[REF]
ISO/SAE DIS 21434: https://www.doc88.com/p-13073341488156.html
- 用户评论
