Coding and communication safety and security measures
Auto industry is facing withrevolution of autonomous driving and information connected, whose dedicated results are longer and more complex coding design, structure, behaviours. Recently many people discuss about how to ensure C coding safety and security quality, well, from state of art, this article will introduce and to check withyou all, any comments are welcome.
Argument: each data and model not come from real projects or company, just state of art.
First: Quality method
From basic, we have to be surefollowing SW metrics and other rules had been obeyed:
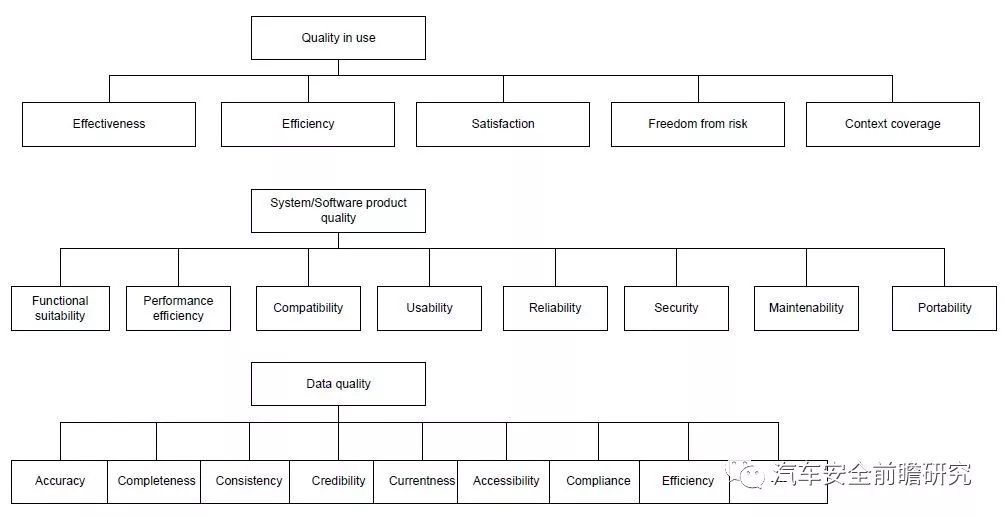
(1) Quality models and measures
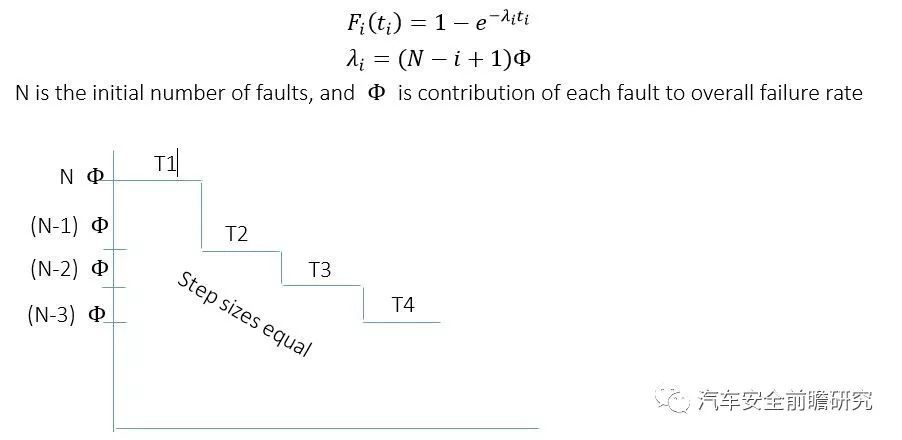
(2) Reliability models
Simplest is JM model, listed asfollowing:
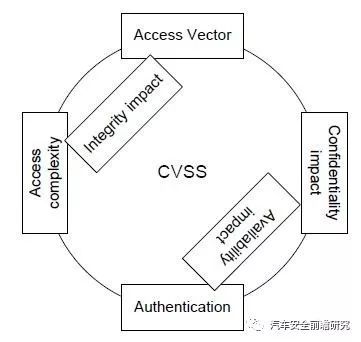
(3) Security metrics
Security, not cyber security,which is the degree to which a product or system protects information and dataso that persons or other products or systems have the degree of data access appropriate to their types and levels of authorization.
State of art, we use Common Vulnerability Scoring System to analysis Coding Security metrics:
(4) Structural and complexitymetrics
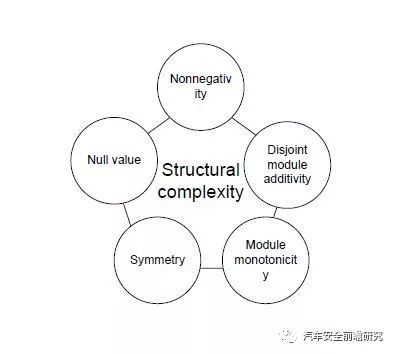
Based on upward properties, weshall use MISRA C to judge if coding in good behaviour and quality. Still thereare two types of MISRA forward: one for manual written codes MISRA2004, anotherfor model based-MISRA-AC-AGC.
Listed following, some example of Polyspace coding rules checker conformity and adoption MISRA-AC-AGC examples
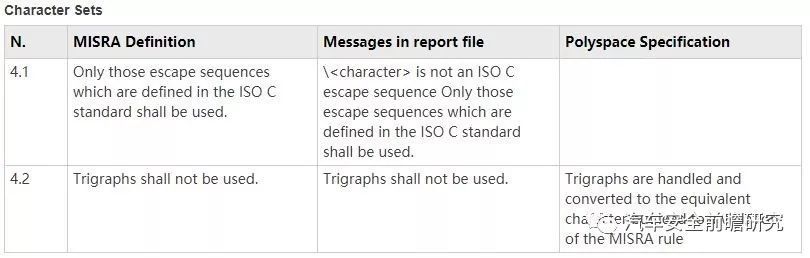
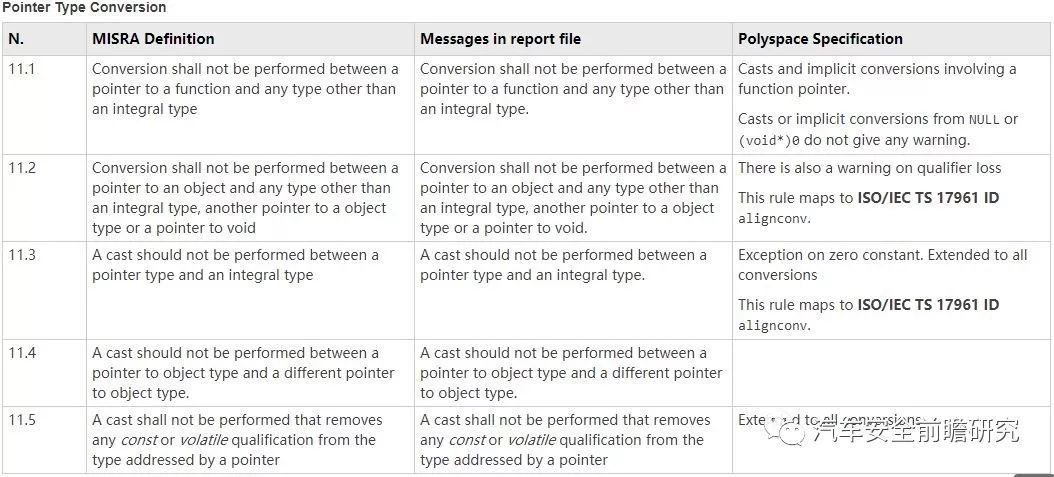
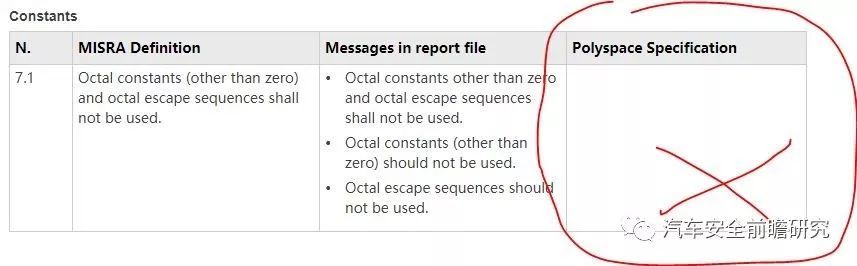
But there are still Polyspace did not cover all of the MISRA C rules, and in real project, functional safetyengineer shall focus on this point.
With time gone by, in Automotive Cybersecurity consideration, we have to use CERT C to manage C coding quality, here due to time limit, I did not dig further into it, but a draft coverage between MISRA C and CERT C given in following, derived from MISRA website:
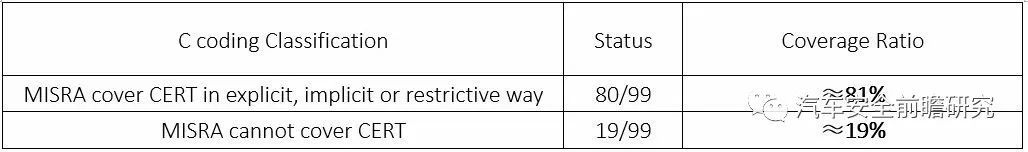
Almost 81% percent of CERT Crules can be covered by MISRA C in some ways, but there still have to bechecked deeper if how they can be covered for cybersecurity engineers, due tofunctional safety engineer will not dig out deeply into coding but directly tosee their QAC or MISRA C status.
Second: Functional Safetyconsideration
Merely C coding safety related faulttypes can be concluded as:
(1) Single bits safety faults
Retrospect ISO 26262-2018,Chapter 5, D2.5.1, safety mechanisms one-bit hardware redundancy, DC=50%, not60% as claimed in Low diagnostic coverage in functional safety.
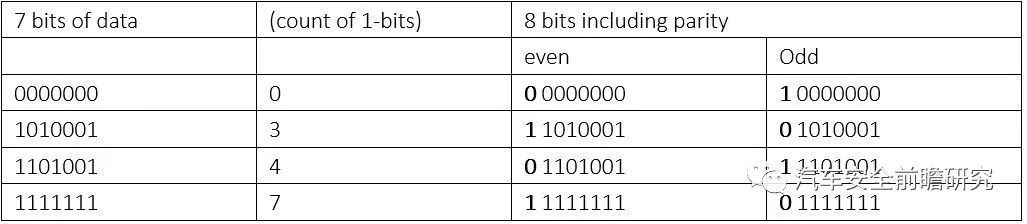
As you can see from table, onebit reserved for parity check.
Apart from which, there is alimitation to parity schemes, a parity bit is only guaranteed to detect an oddnumber of bit errors. If an even number of bits have errors, the parity bitrecords the correct number of ones, even though the data is corrupt.
Final thing to highlight, evenparity is one case for CRC, polynomial to be x+1
(2) two-bits errors, Ones orZeros number faults, or distance faults
Retrospect ISO 26262-2018,Chapter 5, D2.5.2, we get multi-bit hardware redundancy as safety mechanism, one case is hamming code.
Hamming codes can detect up to two-bit errors or correct one-bit errors without detection of uncorrectederrors. Usually, it is are a class of binary linear codes. For each integerr>=2, there is code with block length n=(2^r)-1 and message lengthk=(2^r)-r-1, which gets hamming code is R=k/n=1-r/((2^r)-1), rating listed as following:
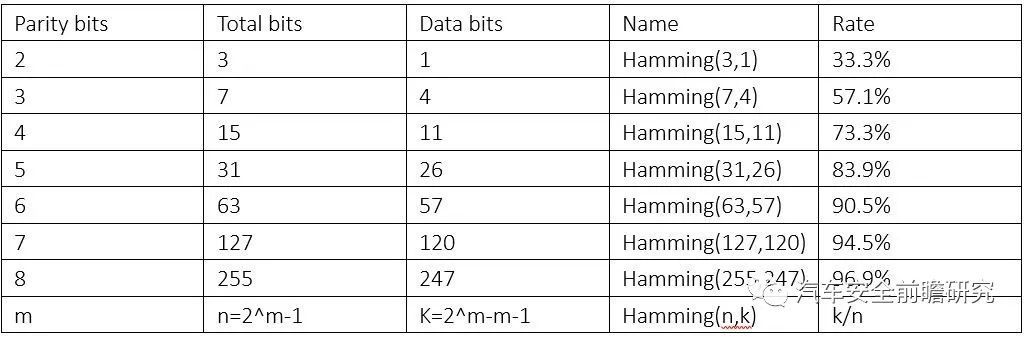
From table, we can see, ratiok/n will be close to 100%.
Here we can dig more into thishamming algorithm:

Detail parity bits and theirposition coverage listed as following:
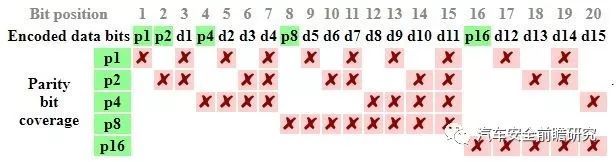
Ref.: Source from wikipedia.com
Apart from upward, we havefollowing important themes to introduce, then you can go further in thisarticle:
(1) Hamming weight
Hamming weight of a string isthe number of symbols that are different from the zero-symbol of the alphabetused, example as following:
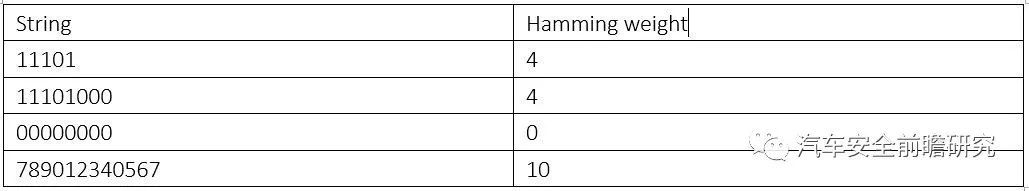
Note: following is one calculation algorithm from WIKI:
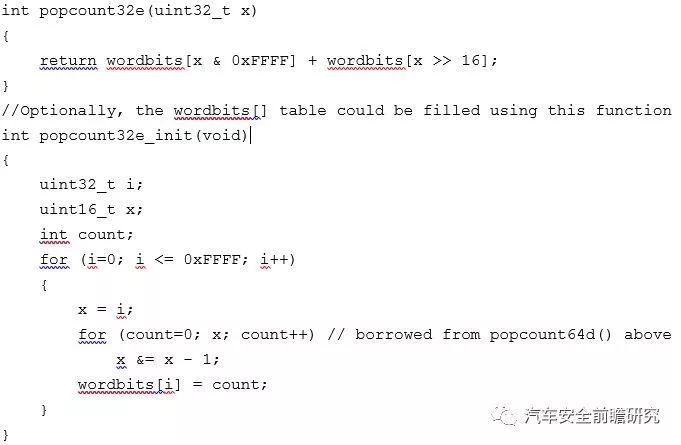
(2) Distance metric
the distance metric has twofamous index:
①Hamming distance: between twostrings of equal length is the number of positions at which the corresponding symbols are different.
Minimum Hamming distance can be calculatedas following method:
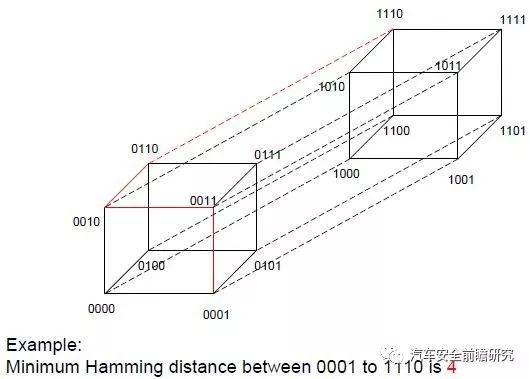
② Levenshtein distance: a string metric for measuring the difference between two sequences. Informally, the Levenshtein distance between two words is min number of single-characteredits (insertions, deletions or substitutions) required to change one word intothe other.
Here you can see Lev distance will be used in more complex strings than hamming distance.
Refered to WIKI, the Levdistance can be following:
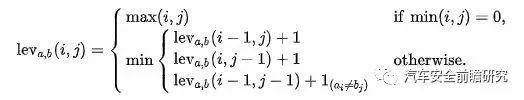
(3) Fault self-recoverymechanisms
Normally used Error correctioncode, types as following
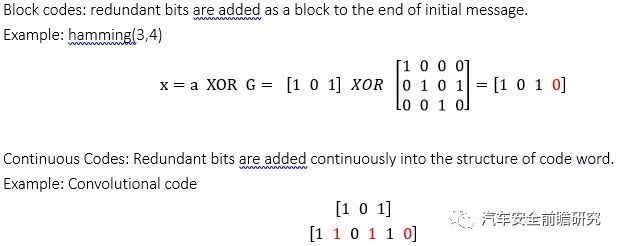
One of common used ECC is LDPC, which is a linear error correcting code, one of its encoder, listed asfollowing:
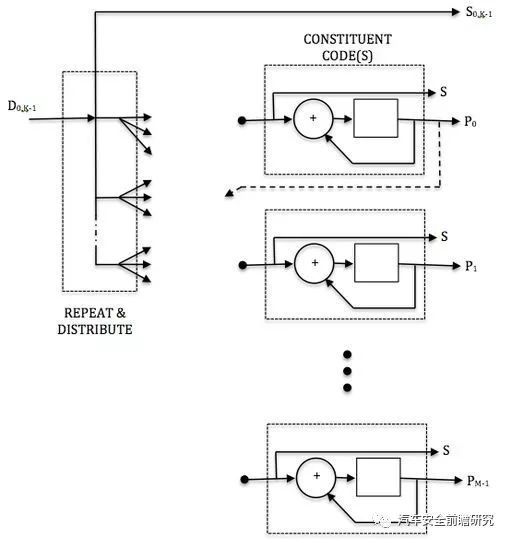
Ref: from WIKI
(3) Ones or zeros each positionfaults, information integrity
One valid safety mechanism is Cyclic Redundancy Checking, originates from functional safety.
From Koopman proposal, there are following recommendations:
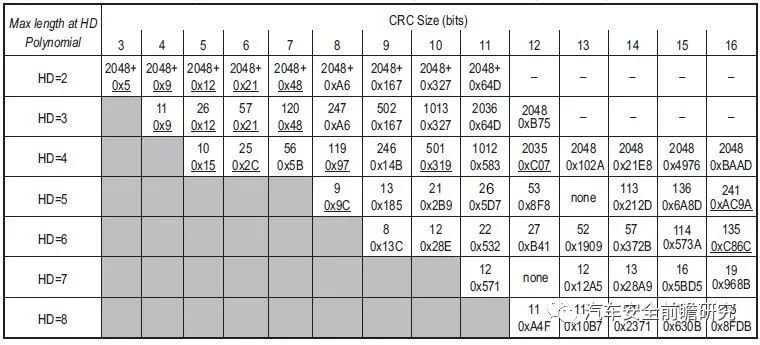
Yet, Auto industry will adoptmore bits than 16bits CRC, proposal adoption listed as following, also combinedfunctional safety ISO 26262 standard recommendation:
CRC-5-USB, usually in tokenpackets; polynomial x5+x2+1(0x12), HD=2, odd-parity-bit
CRC-8-AutoSAR, usually in opensafety; polynomial x8+x5+x3+x2+x+1(0x2F or 0x97), HD=4, even-parity-bit
CRC-10, usually in bank ATM;polynomial 0x233 or 0x319, HD= 4, even-parity-bit
CRC-15-CAN, used in CAN communication; polynomial 0x4599, HD=5, even-parity-bit
CRC-16-CCITT, used bluetooth andin AutoSAR, polynomial 0x1021, even-parity-bit
CRC-24, used in FlexRAY communication; polynomial 0x5D6DCB, HD=6, even-parity-bit
CRC-11, used in FlexRAY header; polynomial 0x385, HD=6, even-parity-bit
CRC-32, used in Ethernet and POSIX, polynomial x32+x26+x23+x22+x16+x12+x11+x10+x8+x7+x5+x4+x2+x+1, HD=10 when in 15bit length;
(4) Frame lost, out of tasks
Originated from ISO 26262, onesafety mechanism called frame counter and time-out monitoring can witness the frame lost or out of tasks failure modes.
And even more, we can combineinformation redundancy, frame counter and time-out monitoring to be E2Eprotection in AutoSAR.
(5) Communication failure modesand End-2-End AutoSAR ASIL D compliant
No matter adaptive or classicalAutoSAR, they share same AUTOSAR_EXP_Functional Safety Measure.
In the information from senderto receiver, their are following failure modes:
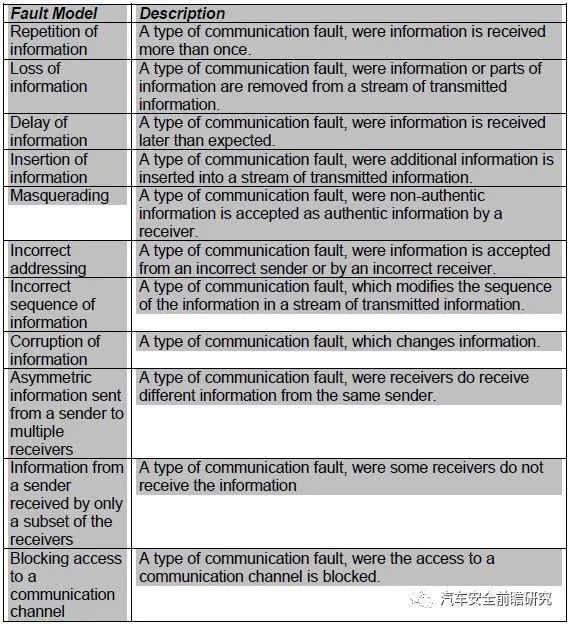
And finally, we can perform onesafety or security analysis towards it:
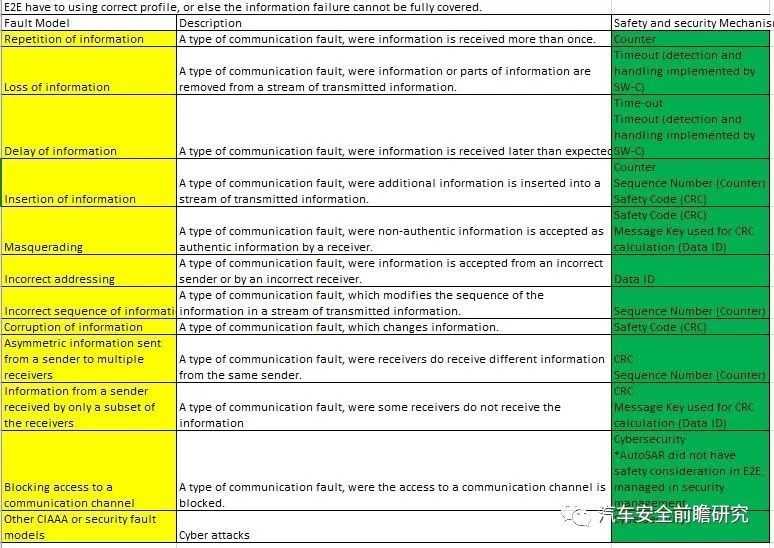
Ensure that AutoSAR shall be incorrect profile, so that all of communication failure modes can have corresponding safety mechanisms
Final: Conclusion
We go through how to manage the communication and C coding safety and security issues, and try to introducesome state of art, including safety and security measures for both of us.
Thanks for your time and see you next time.
[Reference]
MISRA C, 2004
WIKI website
Software Metrics: A rigorous andPractical Approach, Third edition, Norman Fenton
ISO 25010
https://ww2.mathworks.cn/help/bugfinder/ug/misra-c-coding-rules.html
https://www.misra.org.uk/Publications/tabid/57/Default.aspx#label-dvg
SAE J1850
AutoSAR Lib
AUTOSAR_EXP_Functional SafetyMeasure.
- 用户评论
